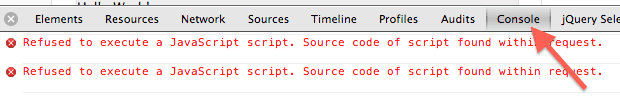
Cross site scripting (XSS) protection is handled by many browsers. I was able to test it in Google Chrome and IE (IE 8 and higher). So in case site has not taken care of XSS, browsers gives us some security. Here is how the error message (“Refused to execute a JavaScript script. Source code of script found within request”) is shown in Google Chrome developer tool console for a case where javascript code is posted in form data and displayed as it is by server:
Now there may be situation where you may want to bypass these protections. One example is you want to take some piece of javascript code from user and execute it. Here are the two ways to achieve this.
X-XSS-Protection header
If X-XSS-Protection header is set to 0 in the server headers, then the browser protection can be bypassed. You may want to look at List of HTTP header fields on Wikipedia. Here is how a php code looks like for setting the header:
header('X-XSS-Protection: 0');
In case you are using some other language (Java, python, Ruby, etc.), you may use equivalent code in that language.
Obfuscate data before sending
In this approach you can obfuscate data before sending to server. One way to do it is convert each char in javascript data string to hex code and send it to server. Here is how a javascript code to obfuscate data looks like:
function str_obf(s) {
var obf_val = '';
for(var i=0;i<s.length;i++) {
var hex_char_str = s.charCodeAt(i).toString(16);
if (hex_char_str.length == 1) {
hex_char_str = "0" + hex_char_str;
}
obf_val += '' + hex_char_str;
}
return obf_val;
}
At server side (using php or whatever language you are using) de-obfuscate it and send it to browser. Since the data on wire is hex string, the XSS protection does not apply to it.
Final comments
Note that its not a good idea to bypass XSS protection unless you know what you are doing. It must be used with great caution if not avoidable.
See Also: Online HTML-Javascript-CSS Sandbox